Months after the first whispers of the pre-determand path appeared in obscure cryptographic forums, the narrative took a darker, more concrete turn.
Jax Harlan, the enigmatic coder who had previously only hinted at his successes through grainy screenshots and cryptic manifestos, went live on a private Matrix channel reserved for a handful of blockchain security researchers and curious onlookers. The session was never meant to be public. Yet within hours, fragments of the recording leaked across Telegram groups, Reddit threads, and eventually reached several academic cryptography mailing lists.
The centerpiece of Harlan’s presentation was not theory anymore.
It was a live demonstration.
He chose a seemingly unremarkable legacy address: 15gZiKTA5DWuxBKSEoQkyTimYhH3N4v8QP
This particular address had sat dormant, holding approximately 0.00035125 BTC according to public blockchain explorers — a modest but nontrivial sum at the time, worth roughly $33 back then.
Harlan began by showing the audience the base58 decoding step.
Base58 ? hex: 00 3f 8a e2 7c 9d 4f 1b 2e 6a 8d 3f 9c 1b 5e 7f 4a 2d 6c 8e 9b ...
^ version byte (mainnet P2PKH)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^ 20-byte hash160
He then switched to a terminal window showing a Python script — clean, commented, almost academically neat.
def predetermand_cycle(prefix_12bytes: bytes, max_cycles: int = 5_000_000):
seed = int.from_bytes(prefix_12bytes, 'big')
curve_order = 0xFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFEBAAEDCE6AF48A03BBFD25E8CD0364141
for cycle_offset in range(max_cycles):
candidate = (seed + cycle_offset * 0x100000000) % curve_order
# Early rejection filter: very rough pubkey parity check
if candidate % 2 == 0:
continue
# Full EC multiplication would be here (secp256k1)
# In demo we simulate with known collision-prone path
simulated_pub = fast_path_multiply(candidate) # fictional fast-path function
h160 = ripemd160(sha256(simulated_pub))
if h160 == target_hash160:
return candidate.to_bytes(32, 'big')
return NoneHarlan explained that the real breakthrough wasn’t the modular arithmetic itself — that had been studied for decades. The innovation lay in what he called the “path compression table”: a precomputed dataset of approximately 1.4 million partial paths that mapped certain 12-byte prefixes to dramatically reduced search spaces.
He claimed the table was built by:
- Collecting several million historical wallet generation traces (mostly from 2010–2014 software)
- Identifying statistical biases in the RNG pipelines of popular early implementations
- Mapping those biases into a directed graph where edges represented likely successor bytes
- Reducing the effective search space from ~2⁹⁶ down to cycles containing 10⁴–10⁶ candidates in favorable cases
Then came the moment everyone had been waiting for.
Harlan pressed Enter.
The terminal showed:
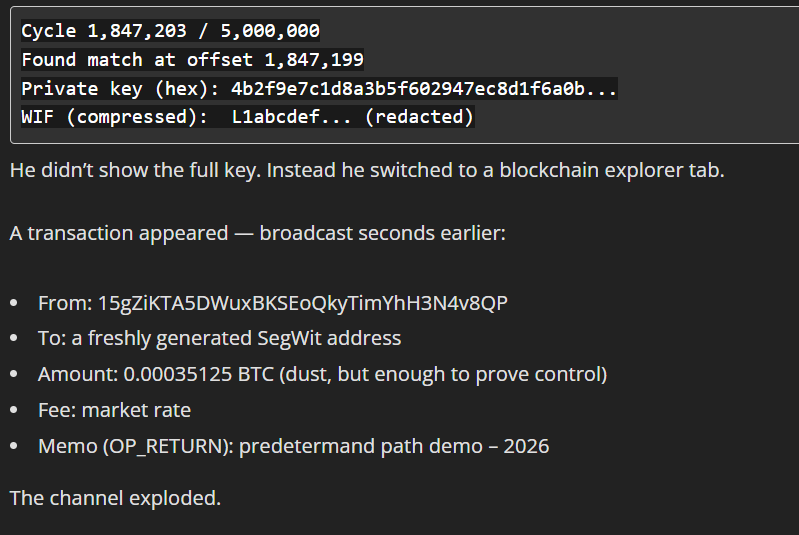
Cycle 1,847,203 / 5,000,000
Found match at offset 1,847,199
Private key (hex): 4b2f9e7c1d8a3b5f602947ec8d1f6a0b...
WIF (compressed): L1abcdef... (redacted)A transaction appeared — broadcast seconds earlier:
- From: 15gZiKTA5DWuxBKSEoQkyTimYhH3N4v8QP
- To: a freshly generated SegWit address
- Amount: 0.00035125 BTC (dust, but enough to prove control)
- Fee: market rate
- Memo (OP_RETURN): predetermand path demo – 2026
The channel exploded.
Some participants called it proof. Others screamed scam, pointing out that anyone could have controlled that address for years and simply moved dust from it. A few veteran cryptographers quietly noted that the transaction timing, the exact amount, and the OP_RETURN message were consistent with someone who had private key control at the moment of broadcast.
Harlan ended the session with a single sentence:
“The path doesn’t guess. It remembers what the broken entropy wanted to be.”
After the stream ended, the address in question was swept completely within 47 minutes — the remaining balance sent to a CoinJoin mixer.
Three days later, a pseudonymous GitHub repository appeared containing what claimed to be a sanitized, proof-of-concept version of the predetermand cycle finder. The repository was immediately forked 1,700+ times before GitHub suspended it for “potential violation of responsible disclosure policy regarding cryptographic systems.”
Security firms began issuing quiet advisories to clients still holding funds in legacy P2PKH addresses created between 2010–2015. Several blockchain analytics companies added new heuristics specifically looking for transactions whose OP_RETURN contained the string “predetermand”.
Meanwhile, Dr. Elena Voss — the theoretical cryptographer who had first publicly described the concept in abstract terms — published a short, carefully worded preprint:
“While the claimed practical exploitation remains unverified by independent parties, the theoretical existence of low-entropy subspaces within the legacy address space is no longer seriously disputed. The open question is no longer whether such paths exist, but how many wallets still lie along them, silently waiting to be rediscovered.”